Editor's note: We have naomi wolf eroticization of consentpublished an updated guide to the Dark Web here.
You may have heard about this mysterious place on the Internet called the 'Deep Web'. Interest in the deep web and dark web arose following a few high profile data leaks, a growing interest in online privacy, references in mainstream media, and the widely publicized FBI investigation into online marketplace Silk Road that exposed the extent of online drug trafficking.
But what is exactly the deep web? Well it's not actually a 'place' but rather anywhere other than the visible web that is crawled, indexed and accessed through links fetched by search engines like Google. The deep web is actually several times bigger than the indexed web, and it encompasses a lot more than the illegal or otherwise questionable activities that it is often associated with – though there's certainly a lot of that going on, too. Let's start by clearing up some of the confusion among the different terms that tend to be thrown around while discussing the Internet's underground.
In simple terms, the Surface Web is anything that a search engine can find by crawling links and identifying content online, while the Deep Web is anything that a search engine can't find. The Dark Web on the other hand merely represents a smaller portion of the deep web that has been intentionally hidden and is inaccessible through standard web browsers.
To exemplify this a bit further, the deep web can actually include things like academic databases, which can be accessed through a normal browser but are not accessible to search engines.
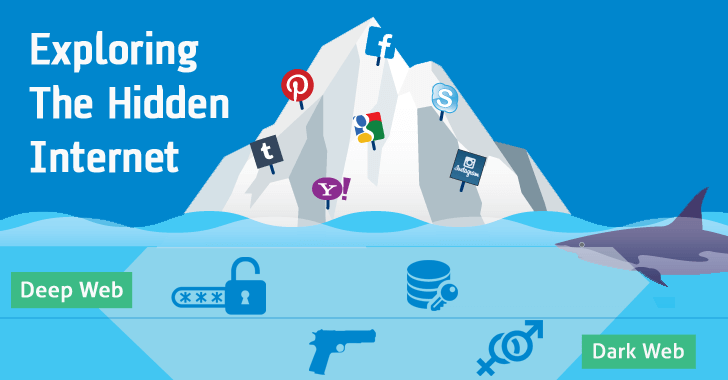
It also includes content within mainstream websites that is simply not set up to be accessed through a search engine. For example content posted on Facebook that is only available to the poster's friends, not the general public, or results for specific queries on a travel booking website – you simply can't get to the content by clicking through links like a search engine would.
The Tor network is the most commonly known place where dark web content resides. This anonymous network consists of thousands of servers located all over the world run by volunteers and online privacy advocates. Its name is an acronym for 'The Onion Router' in reference to its namesake routing technique, which creates a path through randomly assigned Tor servers, or nodes, before reaching whatever website you are visiting. During this process data packets are wrapped in successive layers of packets that get "peeled off" at each node until reaching the destination.
Here is a more technical explanation, but in concise terms, the result is that no one node knows the complete path between your computer and a website, only the last place the packet was, and the next place it will be. This makes it almost impossible for anyone to trace the traffic back to you.
While finding content on the dark web can take time and plenty of patience, technically, accessing the Tor network isn't that complicated at all. You simply need to download and install the Tor browser available for Windows, macOS, and Linux. It is no different from installing any other piece of software and it's very simple to use as it's just a modified version of Firefox.
If you're serious about the security of whatever it is you're doing on the dark web, it's worth running an entirely separate environment from your main computer and internet connection. Tails OS is a bootable operating system that's already preconfigured to maximize privacy and that you can run from a USB stick or a virtual machine. Tails has an installation wizard that guides you step-by-step through the process of setting up the software so that shouldn't pose much of a challenge either. Tails received a lot of press when it was disclosed that Edward Snowden was using it to avoid NSA snooping. Its sole purpose is preserving your privacy and anonymity online by relying on the Tor network and other tools to keep your activity secret.
Layering your location by starting at a random Wi-Fi hotspot and then connecting to a VPN before loading Tor will greatly increase your odds of anonymity.
We have written a more thorough, dedicated article to keeping yourself safe while surfing the seedy underbelly of the web. You can read that here.
 Philips now allows customers to 3D print replacement parts
Philips now allows customers to 3D print replacement parts
 Tesla: Claims of unintended acceleration are 'completely false'
Tesla: Claims of unintended acceleration are 'completely false'
 Americans now trust ads more than news and who can blame them?
Americans now trust ads more than news and who can blame them?
 Watching this robot print and burn Donald Trump's tweets is oddly satisfying
Watching this robot print and burn Donald Trump's tweets is oddly satisfying
 NYT Connections hints and answers for May 18: Tips to solve 'Connections' #707.
NYT Connections hints and answers for May 18: Tips to solve 'Connections' #707.
 Facial recognition company scraped billions of photos to help the cops
Facial recognition company scraped billions of photos to help the cops
 Everything coming to Amazon Prime Video in February 2020
Everything coming to Amazon Prime Video in February 2020
 AppleTV's 'Little America' is full of must
AppleTV's 'Little America' is full of must
 UGREEN Nexode 25000mAh 200W power bank drops to $79.99 at Amazon
UGREEN Nexode 25000mAh 200W power bank drops to $79.99 at Amazon
 Facebook just lost a court fight to cover up possible privacy abuses
Facebook just lost a court fight to cover up possible privacy abuses
 Best robot vacuum deal: Eufy Omni C20 robot vacuum and mop $300 off at Amazon
Best robot vacuum deal: Eufy Omni C20 robot vacuum and mop $300 off at Amazon
 Apple reportedly backed off encrypting iCloud data after pressure from the FBI
Apple reportedly backed off encrypting iCloud data after pressure from the FBI
 Amazon, Microsoft and IBM get hospital records in big data deals
Amazon, Microsoft and IBM get hospital records in big data deals
 Corgi wearing a mermaid tail is the real queen of the sea
Corgi wearing a mermaid tail is the real queen of the sea
 Elaborate 'Beauty and the Beast' promposal is like a real life fairytale
Elaborate 'Beauty and the Beast' promposal is like a real life fairytale
 Everything coming to Amazon Prime Video in February 2020
Everything coming to Amazon Prime Video in February 2020
 How Britain's new child privacy protections will impact the internet
How Britain's new child privacy protections will impact the internet
 The 'recession indicator' meme, explained
The 'recession indicator' meme, explained
 Huawei's Google Maps alternative is TomTom
Huawei's Google Maps alternative is TomTom
Can you find the cats hiding in this Latvian mayor's office?20 wines you need to drink this fallThis man embarked on an insane international quest for the new iPhoneFormula One star Jenson Button is confused by all the Pokémon zombies in SingaporeNow we know exactly what's inside the iPhone 7 in place of the headphone jackGreat white shark spotted jumping out of water just feet from surfersWe asked street style stars to guess British films and TV shows from just the outfitsHow to watch the 'Hearthstone' Americas Summer ChampionshipTwitter's NFL debut impresses despite some problemsThe 5 'One Night in Karazhan' cards that completely change 'Hearthstone' playPaddleboarding enthusiast Orlando Bloom finally made his Instagram publiciOS 10 gets more SnapchatJane Goodall says Trump's antics 'remind me of male chimpanzees'Watch Leslie Jones watch 'Captain America' and feel your soul rise with joy'Westworld' could be the cure for your 'Game of Thrones' nostalgiaThis is what a comet disintegrating in space looks likeBest Nintendo Switch 2 accessories: Hori Piranha cam, MicroSD Express cardsThe 5 'One Night in Karazhan' cards that completely change 'Hearthstone' playTeacher lowers grade for Native American students who sat during Pledge of AllegianceNo regretsy: New design inspo from Down Under's hidden Etsy gems Warren Buffett: Bitcoin is like a seashell or something Can't go home for Thanksgiving? Here are 11 stock photos you can argue with Most Airbnb guests worry about hidden cameras 'Crying Jordan' comes to life at Medal of Freedom award ceremony Like 'Detective Pikachu', these Pokémon phone cases are out for your childhood FTC split on punishing Mark Zuckerberg in settlement with Facebook Verizon wants to sell Tumblr two years after acquiring it 'Avengers: Endgame' sinks a long Racists react after Trump disavows the 'alt Chrissy Teigen once again shuts down Twitter trolls 8 quotes from Trump's New York Times interview that are Trump AF 'Game of Thrones' Episode 4 recap: A disappointing middle Voting, cyber and political experts write letter demanding Russia hacking investigation The Ad Council wants to remind everyone that patriotism is about celebrating diversity Google unveils cheaper Pixel 3a and 3a XL, starting at $399 'Game of Thrones' Season 8's fourth episode had no MVP and here's why Tesla's self Somehow a Starbucks coffee cup appeared on 'Game of Thrones' 23 hilarious yearbook quotes from the class of 2019 YouTube 'conspiracy': Rogue engineer reveals secret plot to kill Internet Explorer
1.0042s , 10193.875 kb
Copyright © 2025 Powered by 【naomi wolf eroticization of consent】,Prosperous Times Information Network